In a rapid evolving cybersecurity environment, security incidents are unavoidable. It makes no difference how big or small your company is, knowing how to handle a security breach is essential and even necessary. The main objective is to reduce damage and stop similar attacks from occurring in the future. In this blog we will cover the fundamental steps of incident response and is intended for beginners who want to know more about this topic.
What is Incident Response?
Incident Response is the process of identifying, researching, and fixing security incidents, like malware infections, data breaches or illegal network access. An effective incident response strategy can help minimize risks, cut down on downtime, safeguard the reputation of your company, and even guard against large financial losses.
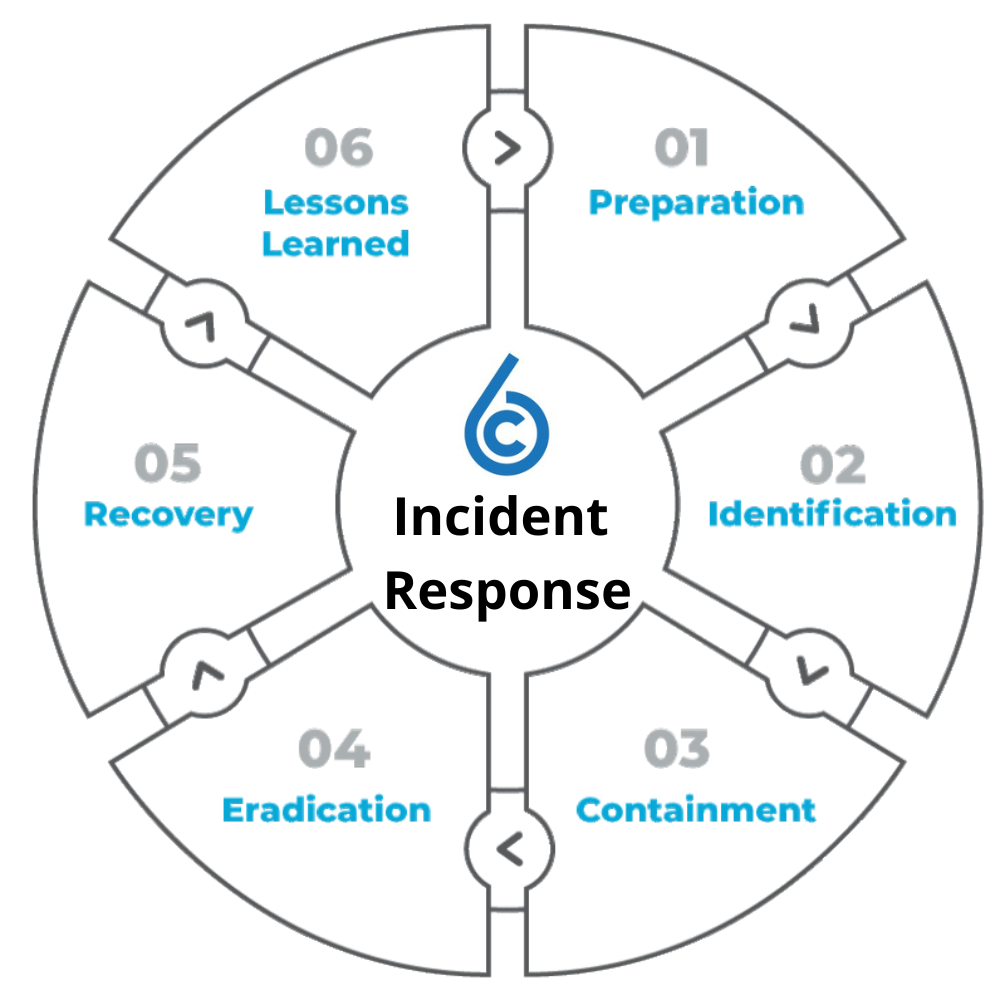
The 6 Key Steps of Incident Response:
- Preparation:
The most crucial step of all is preparation. Having a solid incident response plan (IRP) in place allows your organization to respond quickly and effectively when an incident occurs. Key elements of preparation include:- Building an Incident Response Team (IRT): Identify key personnel responsible for incident response, including security engineers, legal advisors, and public relations experts.
- Training and Drills: Regularly train the team and conduct incident response simulations to ensure everyone knows their roles.
- Create Playbooks: Develop detailed guides for responding to specific incident types, such as malware attacks, phishing, or ransomware.
- Identification:
This phase is all about recognizing that an incident has occurred. Security tools like Intrusion Detection Systems (IDS), antivirus software, and log monitoring solutions can help detect suspicious activities. During this step, the focus is on:- Identifying Indicators of Compromise (IoCs): Look for signs such as unusual traffic patterns, unauthorized logins, or strange file system changes.
- Prioritizing Incidents: Not all incidents have the same level of severity. Triage them based on their potential impact and scope.
- Containment:
Once an incident is identified, it’s crucial to contain the breach to prevent further damage. Containment strategies can be divided into short-term and long-term approaches:- Short-Term Containment: Act quickly to stop the attack. This could involve isolating affected systems from the network or disabling compromised accounts.
- Long-Term Containment: After stabilizing the situation, focus on creating temporary fixes (such as patching vulnerabilities or implementing additional monitoring) to prevent further exploitation while the root cause is investigated.
- Eradication:
After containment, you must remove the threat entirely. This phase involves:- Identifying the Root Cause: Determine how the breach occurred (e.g., exploiting unpatched software, phishing, or insider threats) and address the vulnerability.
- Removing Malicious Artifacts: Clean up malware, delete infected files, and close any backdoors or unauthorized access points used by attackers.
- Recovery:
In the recovery phase, your goal is to safely restore affected systems and return to normal business operations. It’s important to ensure that:- System Integrity is Verified: Ensure that the systems are free from malware and that no unauthorized changes have been made.
- Monitor for Residual Threats: Continue to monitor for any lingering threats or anomalies that may indicate the attacker still has access.
- Gradual Restoration: Bring systems back online gradually, starting with the most critical ones. Continue monitoring to detect any issues.
- Lessons Learned:
The final step in the incident response process is reviewing and learning from the incident. This step is often overlooked but is critical to improving your response efforts in the future. Key actions include:- Post-Incident Review: Hold a meeting with the IRT to discuss what went well and what can be improved. Document everything.
- Update the IRP: If weaknesses were discovered in your response strategy, update the incident response plan to fix them.
- Employee Training: If human error (e.g., clicking a phishing link) contributed to the breach, consider implementing more comprehensive security awareness training.
Why Having an Incident Response Plan Matters
Without a well-prepared incident response plan, breaches can spiral out of control, causing immense financial and reputational damage. A strong IRP helps organizations:
- Minimize data loss and system downtime.
- Control the narrative and manage public relations during an incident.
- Comply with regulations such as GDPR or HIPAA, which require organizations to have specific measures in place to protect sensitive data.
Conclusion
Incident response is a vital part of cybersecurity. Being prepared, having the right tools, and knowing how to act quickly can make all the difference in minimizing the impact of a breach. By continually updating and refining your incident response strategy, you can stay one step ahead of attackers and ensure that your organization is ready to handle security incidents when they occur.
