In the continuously shifting tactics in cybersecurity, some of the most significant breaches originate from endpoints, making it essential for small to medium enterprises (SMEs) to strengthen their endpoint protection. There is no doubt that using Windows Local Administrator Password Solution (LAPS) together with Microsoft Intune is one of the best approaches towards the improvement of security at the endpoint level. Together with Intune, it creates an efficient and secure solution when it comes to dealing with local administrator counterparts in your organization that has a cloud-first environment with Intune-managed devices.
What is Windows LAPS?
Windows LAPS is a tool developed by Microsoft that self-manages local administrators’ passwords on devices that are domain-joined. It comes up with a different complicated password for every machine and stores them safely in the Active Directory (AD) to slow down or decrease the attacker’s potential to move from one device to another.
Why Avoid Using the Default Administrator Account in Windows?
The default administrator account in Windows, while convenient, presents significant security risks. Here’s why it is crucial to avoid using this account in your security practices:
1. Predictable SID (Security Identifier)
Every user or group in Windows has a unique Security Identifier (SID). The SID for the default Administrator account is well-known and consistent across all Windows installations:
- Predictable Target: Attackers can use this predictable SID to directly target the default Administrator account, making it a prime target for attacks. Even if you change the name of the Administrator user.
- Ease of Exploitation: Knowing the SID means that attackers can easily script attacks against this account, increasing the likelihood of successful exploitation.
2. Common Target for Brute Force Attacks
The default Administrator account exists on all Windows systems, making it a common target for brute force attacks:
- Universal Presence: Since this account is universally present, attackers often focus their efforts on breaking into it.
- Brute Force Vulnerability: Attackers use automated tools to try multiple password combinations against this account, which can lead to a successful breach if the password is weak or has not been changed regularly.
3. Difficulties in Password Management
Managing a single password across multiple devices presents several challenges:
- Password Reuse: Using the same password for the default administrator account across multiple devices increases the risk of password reuse attacks. If one device is compromised, all others with the same password are also at risk.
- Complexity of Rotation: Regularly changing the password for the default Administrator account across all devices is cumbersome and error-prone, making it difficult to maintain strong, unique passwords for each device.
4. Lack of Accountability
Using a generic administrator account can obscure accountability:
- Indistinguishable Activity: Actions performed by the default administrator account are not tied to a specific individual, making it challenging to trace activities back to a particular user.
- Reduced Auditing Effectiveness: Auditing and monitoring become less effective when all activities are logged under a generic account, hindering the ability to detect and respond to malicious actions.
Therefore, it is mandatory to make sure that any local account apart from your managed local administrator is disabled. This can be achieved by having a script run through all your devices’ local accounts and disabling them except for the one you are managing.
Here’s a sample script to disable unnecessary local accounts:
# Specify the accounts that should not be disabled (example: adm)
$exemptAccounts = @("adm")
# Get all local user accounts
$localAccounts = Get-LocalUser
# Disable accounts that are not exempt
foreach ($account in $localAccounts) {
if ($exemptAccounts -notcontains $account.Name) {
try {
Disable-LocalUser -Name $account.Name
Write-Output "Disabled local account: $($account.Name)"
} catch {
Write-Output "Failed to disable account: $($account.Name)"
}
}
}
Why Use LAPS with Intune?
Integrating LAPS with Microsoft Intune offers several key benefits:
- Enhanced Security: By ensuring each local admin password is unique and regularly rotated, the risk of password reuse attacks is minimized.
- Simplified Management: Intune allows centralized management and monitoring of LAPS policies without the need for additional infrastructure.
- Compliance and Control: Regular password rotation and detailed audit trails help maintain compliance with security policies and regulations.
Deploying a Local User Account and Adding the Local User Account to the Administrators Group through Intune
Before implementing LAPS, ensure there is a managed local admin account configured on all devices. If not already available and configured, follow these steps to deploy a local admin account through Intune (example ‘adm’ user) or just locally create an account that is a member of the Administrators Group:
1. Create a Local User Account
- Navigate to the Microsoft Intune admin center.
- Go to Devices > Configuration profiles > Create profile.
- Select Windows 10 and later as the platform and choose Templates > Custom.
- Configure the following OMA-URI settings to create a local admin account and replace the Value with the desired initial password (make this strong):
- OMA-URI = ./Device/Vendor/MSFT/Accounts/Users/adm/PasswordData Type = StringValue = *Password string*
- Ensuring the above user is deployed with a strong password is very important; any misconfiguration after this could allow a local user without a password to remain configured on your endpoints.
Assign the Profile to Devices
Assign the configuration profile to the appropriate device groups to ensure the local admin account is created on all targeted devices.
2. Add the Local User Account to the Administrators Group
- Create a new configuration profile in the Microsoft Intune Admin center
- Go to Devices > Configuration profiles > Create profile.
- Select Windows 10 and later as the platform and choose Templates > Custom.
- Configure the following OMA-URI settings to add the local admin account to the Administrators group:
- OMA-URI = ./Device/Vendor/MSFT/Accounts/Users/adm/LocalUserGroupData Type = IntegerValue = 2
Assign the Profile to Devices:
Assign the configuration profile to the appropriate device groups to ensure the local admin account is created on all targeted devices.
3. Monitor Deployment
Use the Intune portal to monitor the deployment status and ensure policies are correctly applied across all devices. Since errors are expected, make sure your test group works as expected functionality over monitoring here. Expected errors here are:
- -2016281112: Read more about this error here.
Implementing LAPS with Intune
Once the local admin account is deployed, follow these steps to implement LAPS with Intune for better password management:
4. Configure LAPS in Intune
- Navigate to the Microsoft Intune admin center.
- Go to Endpoint Security > Account Protection > Create Policy
- Select Windows 10 and later as the platform and choose Local admin password solution (Windows LAPS)
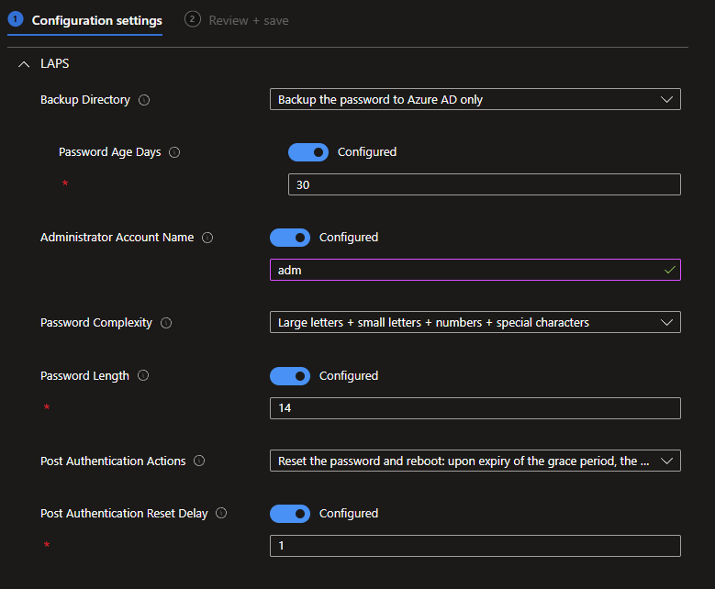
- Configure the following settings:
- Backup Directory
- Administrator Account Name
- Password Complexity
- Password Length
- Post Authentication Actions
- Post Authentication Reset Delay
5. Assign the Profile to Devices
Assign the configuration profile to the appropriate device groups.
6. Monitor Deployment
Use the Intune portal to monitor the deployment status and ensure policies are correctly applied across all devices.

How to Retrieve a LAPS Password for an Enrolled Device
1. Entra ID
Navigate to the Entra ID portal and click on Devices > Overview > Local Administrator Password Recovery and search your device by name:

2. Intune Admin Center
Navigate to the specific device you require the LAPS password from and navigate to the Local Admin Password section to show the local admin password.
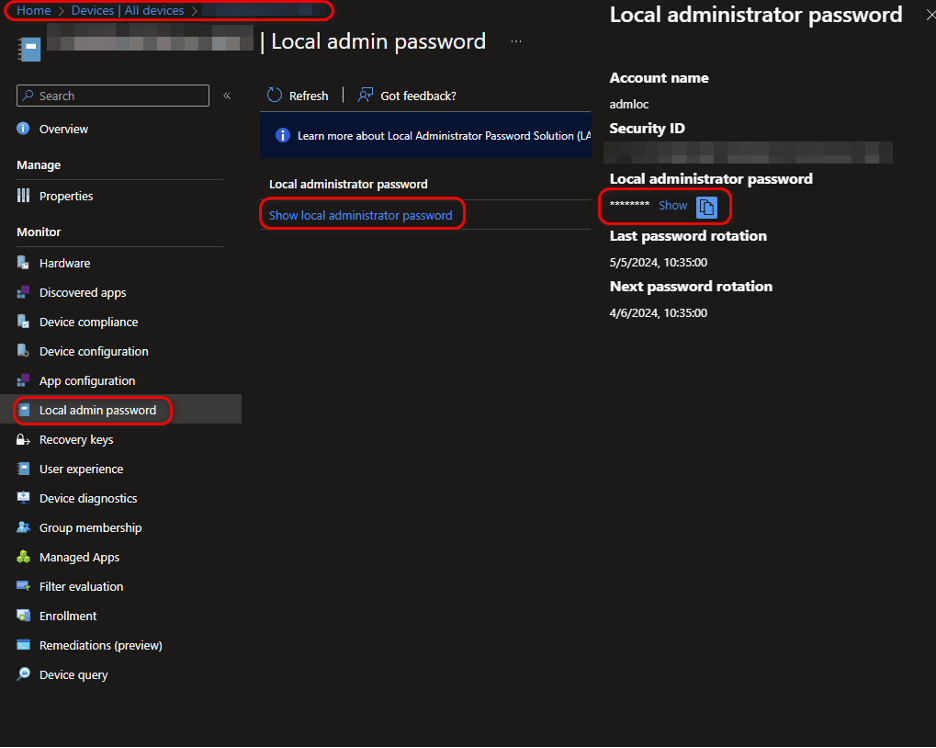
Expected result on the Client side:

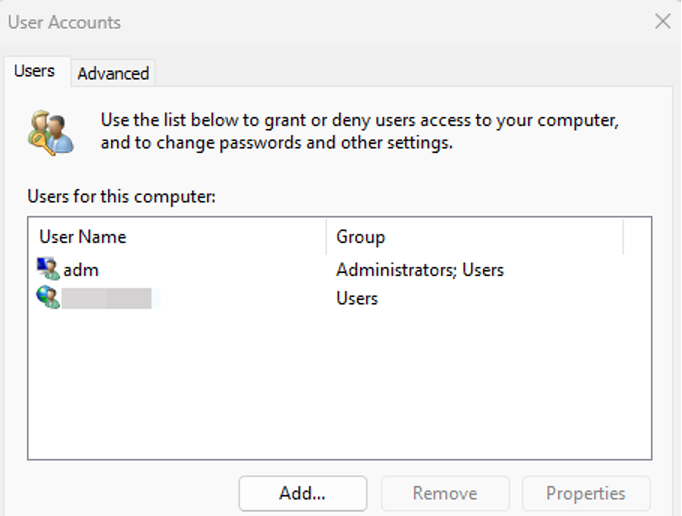
Conclusion
Integrating Windows LAPS with Microsoft Intune offers a robust strategy to address local administrator passwords and improve endpoint protection. Thus, in terms of security, businesses can make a great leap forward and decrease the activity of hackers by managing the default admin account and its quite expected SID. In view of the ever-becoming complex cyber threats, turning to tools such as LAPS will always put your organization in a better posture of dealing with such incidents.
For organizations that use Microsoft 365, incorporating LAPS with Intune is a wise step for improving the security and administration of the IT infrastructure among SMEs. Therefore, by following the outlined procedures, one can reduce vulnerability to cyber threats. The next level of security thus lies in completely eradicating the local administrative accounts and enforcing the principle of least privilege. They also help minimize access and utilization of restricted administrative privileges, thus improving the security system.
